ZachXBT Exposes $2M Impersonation Scammer
Blockchain sleuth ZachXBT has unmasked a Canadian scammer who allegedly stole more than $2 million in cryptocurrency by posing as a Coinbase customer support representative, underscoring how social engineering has become one of the most dangerous threats facing exchange users today.
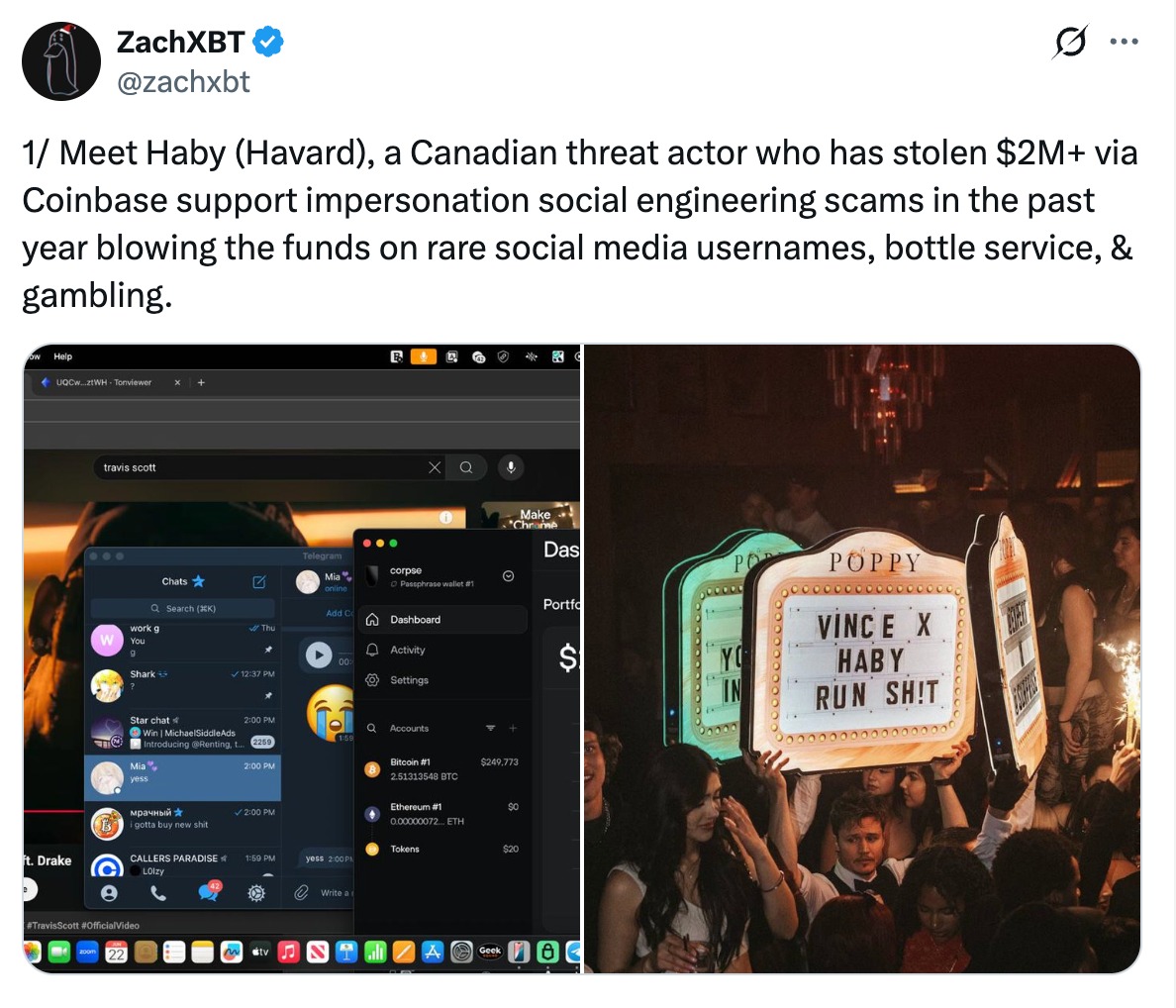
Image Source: ZachXBT
A Year-Long Fake Support Operation
According to ZachXBT’s latest investigation, the alleged scammer operated under the aliases “Haby” and “Havard” while running a year-long scheme targeting Coinbase users across multiple countries. Instead of deploying malware or exploiting smart contract bugs, he relied on old-fashioned deception: cold calls, spoofed contact details, and high-pressure scripts designed to make victims believe their accounts were at immediate risk. Victims were reportedly contacted by phone or messaging apps by someone claiming to be from Coinbase’s help desk, often referencing fabricated “security alerts” or “suspicious withdrawals” to create urgency. Under the guise of fixing the problem, the scammer allegedly walked users through steps that handed him effective control of their accounts or persuaded them to transfer funds directly to wallets he controlled.
How ZachXBT Followed the Money
ZachXBT pieced the case together using a mix of on-chain forensics and open-source intelligence, matching blockchain transactions with the scammer’s own digital footprint. Screenshots from Telegram chats, public boasting on social media, and leaked wallet balances became clues that allowed him to connect specific addresses to stolen funds and, ultimately, to a real-world identity in Abbotsford, near Vancouver, Canada. One key breakthrough came from a screenshot posted on December 30, 2024, in which “Haby” bragged about stealing 21,000 XRP from a Coinbase user, inadvertently revealing an XRP address tied to several other thefts. By following flows from that address, ZachXBT linked multiple Coinbase-related compromises, eventually pushing the tally of confirmed losses to more than $2 million. The stolen XRP and other assets were frequently routed through instant exchange services to convert them into bitcoin, then split across multiple wallets and, in many cases, sent to online gambling platforms. ZachXBT shared that transaction timing, wallet balances and screenshots of lavish spending on nightlife and rare Telegram usernames all lined up with outflows from these addresses, turning scattered clues into a coherent pattern of abuse.
Leaked Call, Leaked Identity
The investigation became even more concrete when a video of a live “support” call surfaced, allegedly capturing the scammer in the middle of one of his social engineering attempts. In the clip, the caller calmly walks a victim through supposed “security steps,” while accidentally exposing a connected email address and Telegram handle that ZachXBT later tied back to the same wallet cluster. Despite repeated attempts to cover his tracks, the scammer’s habit of flaunting stolen wealth online undermined his operational security. Location hints in selfies and story posts helped narrow his base of operations to specific neighbourhoods in British Columbia, adding pressure on Canadian authorities to respond.
A Wider Pattern of Coinbase Impersonation
This case is a part of a broader wave of support-impersonation attacks against Coinbase users that ZachXBT has been documenting over the past year. In an earlier report, he estimated that Coinbase users lost around $65 million to social engineering scams in just one month, driven largely by fake “customer care” contacts that convinced victims to hand over control of their accounts. In June, he also exposed another scammer, known as “Daytwo” or “PawsOnHips,” who allegedly ran a small call-center-style operation that stole more than $4 million from Coinbase users through similar tactics. In that case, too, much of the stolen money was funneled into online casinos and luxury spending.
How Users Can Protect Themselves
The latest exposure serves as a stark reminder that, in crypto, the weakest link is often human rather than code. Social engineering scams typically start with unsolicited calls, texts or emails that appear to come from a trusted brand, then escalate with warnings about urgent “security issues” that must be fixed immediately. Users are urged to ignore unsolicited contact, hang up on unexpected calls, and reach support only through official in-app or website channels, especially when dealing with anything involving passwords or withdrawals.





Leave a Comment