ZachXBT Flags New Ledger Data Breach via Global‑e
ZachXBT flagged a fresh data breach tied to Ledger’s e‑commerce partner Global‑e, exposing customer names and contact details. The incident once again highlights a painful truth for hardware wallet users: even when your private keys are safe, your personal data often is not.
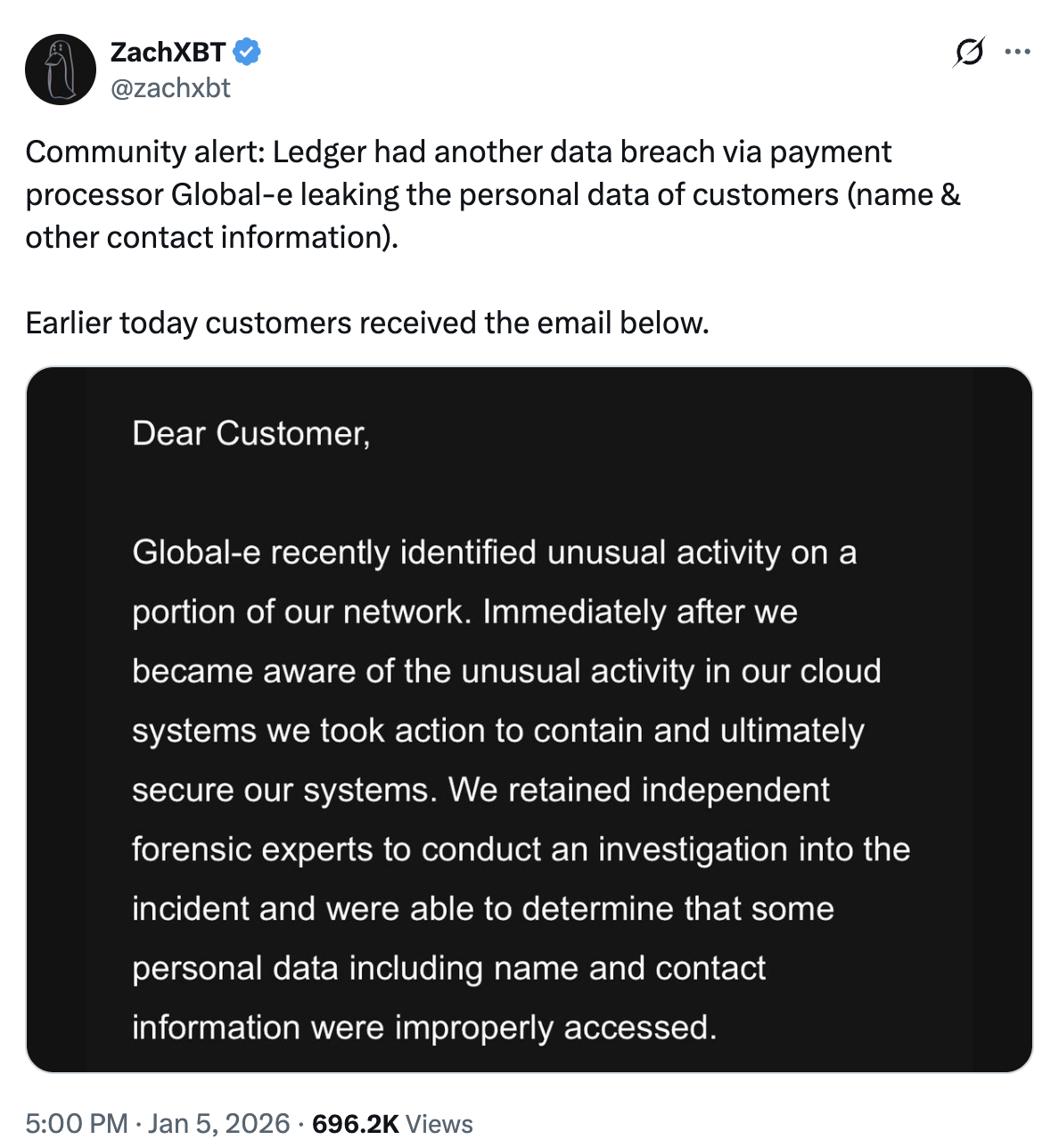
Image Source: ZachXBT
What ZachXBT Exposed?
According to notifications sent to affected users, Global‑e, a third‑party payment and e‑commerce processor used by Ledger, suffered unauthorized access to a cloud-based system containing shopper order data. Only customers who purchased through Ledger’s online store using Global‑e as the merchant of record are in the potential impact zone, but neither Ledger nor Global‑e have disclosed how many people that includes. ZachXBT brought the situation to wider attention by sharing details of the breach with the crypto community, amplifying screenshots of the notification emails and warning that exposed data could be weaponized in targeted phishing attacks. Those messages, sent by Global‑e, confirm that names and contact information such as email addresses, phone numbers, and shipping details were accessed by an unauthorized party.
What Was Compromised?
Both Ledger and Global‑e stress that the breach is limited to personal and order data, not wallet secrets. Ledger has clarified that its hardware devices, software wallets, and core infrastructure remain uncompromised, and that Global‑e never had access to 24‑word seed phrases, private keys, wallet balances, or any “on‑chain” secrets. Equally important, Global‑e says no payment card information or account credentials were exposed in this incident. The data set appears to focus on typical e‑commerce records: customer identity, contact channels, and details about past orders placed via Ledger’s online store. That may sound less dramatic than a direct wallet hack, but for attackers who specialize in social engineering, it is exactly the kind of intelligence they want.
Why This Breach Matters for Ledger Users
For Ledger customers, this is not the first time their off‑chain identity has been dragged into the spotlight. A 2020 incident involving a rogue Shopify employee exposed data from roughly 270,000 Ledger buyers, leading to a flood of phishing emails and even reports of physical threats tied to leaked home addresses. In 2023, Ledger also dealt with a supply‑chain attack that injected malicious code into its Ledger Connect Kit, enabling “wallet drainer” exploits until the issue was patched. This latest Global‑e breach feeds into a growing fear that multiple leaks, over several years and across different partners, are slowly building a detailed map of who owns crypto, where they live, and how to reach them. Security firms have already reported tens of millions of dollars lost annually to phishing attacks that rely on exactly this kind of harvested data.
How Users Should Protect Themselves Now
Ledger is urging customers to stay hyper‑vigilant and to treat any unexpected communication as suspicious, no matter how convincing it looks. The company reiterates its golden rule: never share your 24‑word recovery phrase with anyone, under any circumstances, and never type it into a website, app, or form claiming to be “Ledger support.” Enabling email filters, using unique addresses where possible, and double‑checking URLs before interacting with any “security alert” can make the difference. The Global‑e episode is a stark reminder that in crypto, self‑custody solves only part of the problem. As long as hardware wallet brands rely on third‑party commerce platforms, the weakest link may not be the blockchain at all, but the ordinary databases quietly holding your name and your inbox.





Leave a Comment